3 Getting Started with Oracle Database Vault
Before you can start using Oracle Database Vault, you must configure and enable it with the Oracle database.
- About Configuring and Enabling Oracle Database Vault in Oracle Database
Oracle Database includes Database Vault when you choose to include a default database in the installation process, but you must configure and enable it before you can use it. - Configuring and Enabling Oracle Database Vault
You can configure and enable Oracle Database Vault based on several scenarios. - Verifying That Database Vault Is Configured and Enabled
TheDBA_DV_STATUS,CDB_DV_STATUS, andDBA_OLS_STATUSdata dictionary views verify if Oracle Database is configured and enabled. - Logging in to Oracle Database Vault from Oracle Enterprise Cloud Control
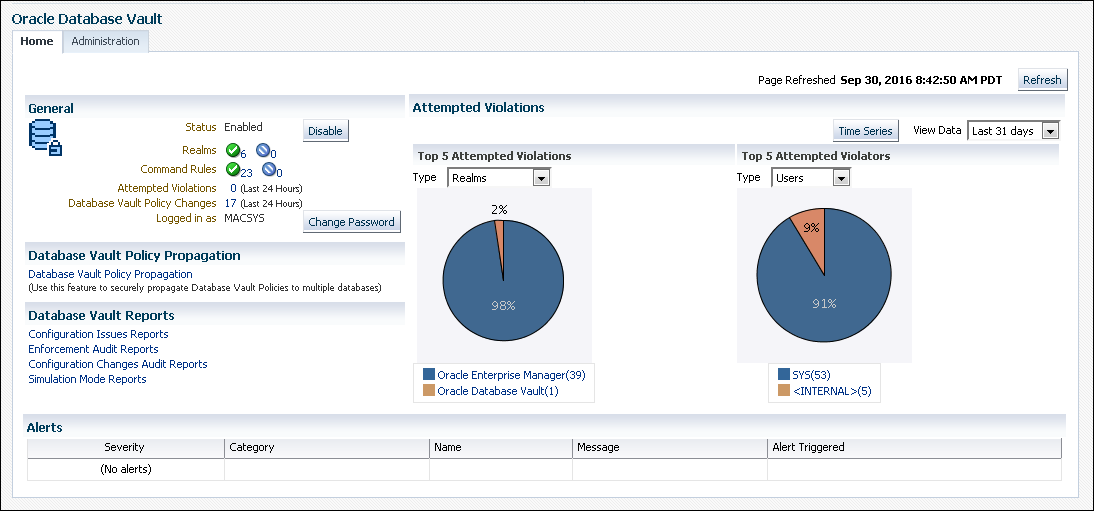
Oracle Enterprise Manager Cloud Control (Cloud Control) provides pages for managing Oracle Database Vault. - Quick Start Tutorial: Securing a Schema from DBA Access
This tutorial shows how to create a realm around theHRschema.
3.1 About Configuring and Enabling Oracle Database Vault in Oracle Database
Oracle Database includes Database Vault when you choose to include a default database in the installation process, but you must configure and enable it before you can use it.
The configuration and enablement process enables Oracle Label Security if it is not already enabled. Oracle Label Security is required for Oracle Database Vault but it does not require a separate license unless you begin using Oracle Label Security separately and create Oracle Label Security policies.
If you create a custom database, then you can use DBCA to install and enable Database Vault for it. The registration process enables Oracle Label Security if it is not already enabled. This procedure applies to the CDB root, application root, and the current pluggable database (PDB), as well as to both single-instance and Oracle Real Application Clusters (Oracle RAC) installations. In a multitenant database, Database Vault must be configured with the CDB root before any of the PDBs can configure Database Vault.
As part of the configuration process, you created the Oracle Database Vault administrative accounts. The Oracle Database Vault configuration recommends four administrative database account names (two primary accounts and two backup accounts) with different passwords for each. These are accounts that hold the Database Vault roles DV_OWNER and DV_ACCTMGR, granted with the WITH ADMIN OPTION clause. Two of these accounts will be used to provision the roles to named users with administrative privileges. Maintaining two backup accounts, one with DV_OWNER and one with DV_ACCTMGR roles, will allow you to recover from the named user losing or somehow misplacing their credentials because SYS, or any other user, will not be able to reset these passwords for users with these roles.
Note:
If you upgraded from a release earlier than Oracle Database 12c, then you disabled Oracle Database Vault to perform the upgrade. After the upgrade process is complete, then you must configure and enable Oracle Database Vault again.If you are migrating a non-Database Vault-enabled Oracle database from a release earlier than release 12c, then you must perform a manual installation of Database Vault.
3.2 Configuring and Enabling Oracle Database Vault
You can configure and enable Oracle Database Vault based on several scenarios.
- About Configuring and Enabling Database Vault
You must configure and enable Oracle Database Vault in the CDB root before you can perform the same action in any of the associated PDBs. - Configuring and Enabling Database Vault in the CDB Root
You can configure and enable Oracle Database Vault with common users who will use the Database Vault administrative roles from the CDB root. - Configuring and Enabling Database Vault Common Users to Manage Specific PDBs
You must configure and enable Oracle Database Vault in the CDB root first, then in the PDBs afterward. - Configuring and Enabling Database Vault Local Users to Manage Specific PDBs
You must configure and enable Oracle Database Vault in the root first, and then in the PDBs afterward. - Configuring and Enabling Oracle Database Vault in an Oracle Real Application Clusters Environment
You can configure Oracle Database Vault for an Oracle Real Application Clusters (Oracle RAC) environment, including each Oracle RAC node. - Creating a Profile to Protect the DV_OWNER and DV_ACCTMGR Users
A profile provides additional protection for users who have been granted theDV_OWNERandDV_ACCTMGRroles. - Manually Installing Oracle Database Vault
Under certain conditions, you must manually install Oracle Database Vault.
Parent topic: Getting Started with Oracle Database Vault
3.2.1 About Configuring and Enabling Database Vault
You must configure and enable Oracle Database Vault in the CDB root before you can perform the same action in any of the associated PDBs.
The common users who have been assigned the DV_OWNER and DV_ACCTMGR roles in the CDB root can also have the same role in the PDBs. PDBs can have Database Vault configured and enabled using the same common users or use separate PDB local users. The DV_ACCTMGR role is granted commonly to the common user in the CDB root. You can grant DV_OWNER locally or commonly to the CDB root common user when you configure and enablement Database Vault with the CDB root. Granting DV_OWNER locally to the common user prevents the common DV_OWNER user from using this role in any PDB.
Parent topic: Configuring and Enabling Oracle Database Vault
3.2.2 Configuring and Enabling Database Vault in the CDB Root
You can configure and enable Oracle Database Vault with common users who will use the Database Vault administrative roles from the CDB root.
UTL_RECOMP PL/SQL package to check the validity of objects. See Oracle Database PL/SQL
Packages and Types Reference.
Related Topics
- Verifying That Database Vault Is Configured and Enabled
- Oracle Database Vault Roles
- Logging in to Oracle Database Vault from Oracle Enterprise Cloud Control
- DV_PATCH_ADMIN Database Vault Database Patch Role
- CONFIGURE_DV General System Maintenance Procedure
- Configuring and Enabling Oracle Database Vault in an Oracle Real Application Clusters Environment
- Resetting Oracle Database Vault Account Passwords
Parent topic: Configuring and Enabling Oracle Database Vault
3.2.3 Configuring and Enabling Database Vault Common Users to Manage Specific PDBs
You must configure and enable Oracle Database Vault in the CDB root first, then in the PDBs afterward.
ORA-47503: Database Vault is not enabled on CDB$ROOT error appears.
Related Topics
- Verifying That Database Vault Is Configured and Enabled
- Oracle Database Vault Roles
- Logging in to Oracle Database Vault from Oracle Enterprise Cloud Control
- DV_PATCH_ADMIN Database Vault Database Patch Role
- CONFIGURE_DV General System Maintenance Procedure
- Configuring and Enabling Database Vault in the CDB Root
- Resetting Oracle Database Vault Account Passwords
Parent topic: Configuring and Enabling Oracle Database Vault
3.2.4 Configuring and Enabling Database Vault Local Users to Manage Specific PDBs
You must configure and enable Oracle Database Vault in the root first, and then in the PDBs afterward.
ORA-47503: Database Vault is not enabled on CDB$ROOT error appears.
3.2.5 Configuring and Enabling Oracle Database Vault in an Oracle Real Application Clusters Environment
You can configure Oracle Database Vault for an Oracle Real Application Clusters (Oracle RAC) environment, including each Oracle RAC node.
Related Topics
Parent topic: Configuring and Enabling Oracle Database Vault
3.2.6 Creating a Profile to Protect the DV_OWNER and DV_ACCTMGR Users
A profile provides additional protection for users who have been granted the DV_OWNER and DV_ACCTMGR roles.
DV_OWNER or DV_ACCTMGR roles are considered critical, privileged, accounts. Typically, these accounts should be considered service accounts and exempt from password lockout requirements. Oracle recommends that you create a custom profile that prevents the account from being locked. In addition, you should audit failed login attempts for these Database Vault-related accounts.
- Log into the database instance as a user who has the
CREATE PROFILEsystem privilege.- For common
DV_OWNERandDV_ACCTMGRusers: Log in to the root of the database instance. - For local
DV_OWNERandDV_ACCTMGRusers: Log in to the PDB in which you created the users.
- For common
- Create a profile similar to the following:
- For common
DV_OWNERandDV_ACCTMGRusers: In the root, create the profile similar to the following:CREATE PROFILE c##dv_profile limit FAILED_LOGIN_ATTEMPTS 5 PASSWORD_VERIFY_FUNCTION ORA12C_VERIFY_FUNCTION PASSWORD_LOCK_TIME 1/1440 CONTAINER=ALL;By setting the
password_lock_timeto 1/1440, you will lock the user account for one minute after five failed login attempts. This ensures yourDV_OWNER-related accounts cannot be permanently locked out. You should adjust the limits to meet your organization or industry standards. - For local
DV_OWNERandDV_ACCTMGRusers: In the PDB, create the profile similar to the following:CREATE PROFILE dv_profile limit FAILED_LOGIN_ATTEMPTS 5 PASSWORD_VERIFY_FUNCTION ORA12C_VERIFY_FUNCTION PASSWORD_LOCK_TIME 1/1440 CONTAINER=CURRENT;By setting the
password_lock_timeto 1/1440, you will lock the user account for one minute after five failed login attempts. This ensures yourDV_OWNER-related accounts cannot be permanently locked out. You should adjust the limits to meet your organization or industry standards.
- For common
- Update the
DV_OWNERandDV_ACCTMGRuser accounts to use this profile.- For common
DV_OWNERandDV_ACCTMGRusers:ALTER USER c##dvowner PROFILE c##dv_profile CONTAINER = ALL; ALTER USER c##dvowner_backup PROFILE c##dv_profile CONTAINER = ALL; ALTER USER c##dvacctmgr PROFILE c##dv_profile CONTAINER = ALL; ALTER USER c##dvacctmgr_backup PROFILE c##dv_profile CONTAINER = ALL; - For local
DV_OWNERandDV_ACCTMGRusers:ALTER USER dvowner PROFILE dv_profile CONTAINER = CURRENT; ALTER USER dvowner_backup PROFILE dv_profile CONTAINER = CURRENT; ALTER USER dvacctmgr PROFILE dv_profile CONTAINER = CURRENT; ALTER USER dvacctmgr_backup PROFILE dv_profile CONTAINER = CURRENT;
- For common
- Connect as a user who has been granted the
AUDIT_ADMINrole. - Create and enable a unified audit policy to track failed logins by any user who has been granted the
DV_OWNERorDV_ACCTMGRrole.- For common
DV_OWNERandDV_ACCTMGRusers: In the root, create a policy similar to the following:CREATE AUDIT POLICY c##dv_logins ACTIONS LOGON; AUDIT POLICY c##dv_logins BY USERS WITH GRANTED ROLES DV_OWNER, DV_ACCTMGR WHENEVER NOT SUCCESSFUL; - For local
DV_OWNERandDV_ACCTMGRusers: In the PDB, create a policy similar to the following:CREATE AUDIT POLICY dv_logins ACTIONS LOGON; AUDIT POLICY dv_logins BY USERS WITH GRANTED ROLES DV_OWNER, DV_ACCTMGR WHENEVER NOT SUCCESSFUL;
- For common
Parent topic: Configuring and Enabling Oracle Database Vault
3.2.7 Manually Installing Oracle Database Vault
Under certain conditions, you must manually install Oracle Database Vault.
Related Topics
Parent topic: Configuring and Enabling Oracle Database Vault
3.3 Verifying That Database Vault Is Configured and Enabled
The DBA_DV_STATUS, CDB_DV_STATUS, and DBA_OLS_STATUS data dictionary views verify if Oracle Database is configured and enabled.
SYS user and users who have been granted the DBA role can query these views.
-
For Database Vault:
-
If you want to find the Database Vault status for the root only or an individual PDB, then query
DBA_DV_STATUS. For example:SELECT * FROM DBA_DV_STATUS;Output similar to the following appears:
NAME STATUS -------------------- ----------- DV_APP_PROTECTION NOT CONFIGURED DV_CONFIGURE_STATUS TRUE DV_ENABLE_STATUS TRUEDV_APP_PROTECTIONrefers to operations control, which automatically restricts common users from accessing PDB local data in Oracle Database multitenant environments. -
If you want to find the Database Vault status of all PDBs in the multitenant environment, then as a common user with administrative privileges, query
CDB_DV_STATUS, which provides the addition of a container ID (CON_ID) field.
-
-
For Oracle Label Security, query the
DBA_OLS_STATUSdata dictionary view.
3.4 Logging in to Oracle Database Vault from Oracle Enterprise Cloud Control
Oracle Enterprise Manager Cloud Control (Cloud Control) provides pages for managing Oracle Database Vault.
3.5 Quick Start Tutorial: Securing a Schema from DBA Access
This tutorial shows how to create a realm around the HR schema.
- About This Tutorial
In this tutorial, you create a realm around theEMPLOYEEStable in theHRsample database schema by using the Oracle Database Vault PL/SQL packages. - Step 1: Log On as SYSTEM to Access the HR Schema
You must enable theHRschema for this tutorial. - Step 2: Create a Realm
Realms can protect one or more schemas, individual schema objects, and database roles. - Step 3: Create a Unified Audit Policy for Realm Violations
You can create unified audit policies for Oracle Database Vault realms, rule sets, and factors. - Step 4: Create the SEBASTIAN User Account
At this stage, only theHRschema and database users, or roles, with direct object grants can manipulate the database objects the realm will protect. Users relying on system privileges cannot. - Step 5: Have User SEBASTIAN Test the Realm
At this stage, usersebastiancan test the realm by trying to query theHR.EMPLOYEEStable. - Step 6: Create an Authorization for the Realm
Next, userSEBASTIANmust be granted authorization to theHR Appsrealm, so that they can access theHR.EMPLOYEEStable. - Step 7: Test the Realm
To test the realm, you must try to access theEMPLOYEEStable as a user other thanHR. - Step 8: View Audit Records from Realm Violations
You should conduct a periodic review of violations on the unified audit policies that you have created. - Step 9: Remove the Components for This Tutorial
You can remove the components that you created for this tutorial if you no longer need them.
Parent topic: Getting Started with Oracle Database Vault
3.5.1 About This Tutorial
In this tutorial, you create a realm around the EMPLOYEES table in the HR sample database schema by using the Oracle Database Vault PL/SQL packages.
You will also learn how to create a unified audit policy to record realm violations and review them.
In the HR schema, the EMPLOYEES table has information such as salaries that should be hidden from most employees in the company, including those with administrative access. To accomplish this, you add the HR schema to the secured objects of the protection zone, which in Oracle Database Vault is called a realm, inside the database. Then you grant limited authorizations to this realm. Afterward, you test the realm to make sure it has been properly secured.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.2 Step 1: Log On as SYSTEM to Access the HR Schema
You must enable the HR schema for this tutorial.
HR sample schema is installed.
Related Topics
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.3 Step 2: Create a Realm
Realms can protect one or more schemas, individual schema objects, and database roles.
EMPLOYEES table in the HR schema.
- Connect to a PDB as a user who has been granted the
DV_OWNERrole. - Create the
HR Appsrealm around theHR.EMPLOYEEStable.
At this stage, you have created the realm but you have not assigned any authorizations to it. Because this is a traditional realm (realm_type => DBMS_MACADM.REGULAR_REALM), any user with direct grants to READ or SELECT from HR.EMPLOYEES will still be able to view this table, but users who rely on system privileges, such as READ ANY TABLE or SELECT ANY TABLE, will not. You will take care of that later on in this tutorial.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.4 Step 3: Create a Unified Audit Policy for Realm Violations
You can create unified audit policies for Oracle Database Vault realms, rule sets, and factors.
After you create a realm, you can create unified audit policies to capture violations of the realm.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.5 Step 4: Create the SEBASTIAN User Account
At this stage, only the HR schema and database users, or roles, with direct object grants can manipulate the database objects the realm will protect. Users relying on system privileges cannot.
HR.EMPLOYEES table. User cmack has been granted the AUDIT_ADMIN role, and through the DBMS_MACADM.AUTHORIZE_AUDIT_ADMIN authorization that you performed earlier, authorized to use the AUDIT_ADMIN role to manage unified audit policies and view unified audit records. You will create the sebastian user account.
Related Topics
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.6 Step 5: Have User SEBASTIAN Test the Realm
At this stage, user sebastian can test the realm by trying to query the HR.EMPLOYEES table.
sebastian has the READ ANY TABLE system privilege, he cannot query the HR.EMPLOYEES table, because the HR Apps realm takes precedence over the READ ANY TABLE system privilege.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.7 Step 6: Create an Authorization for the Realm
Next, user SEBASTIAN must be granted authorization to the HR Apps realm, so that they can access the HR.EMPLOYEES table.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.8 Step 7: Test the Realm
To test the realm, you must try to access the EMPLOYEES table as a user other than HR.
HR from accessing its own objects.)
The SYSTEM account normally has access to all objects in the HR schema because it has the SELECT ANY TABLE privilege, but now that you have safeguarded the EMPLOYEES table with Oracle Database Vault, this is no longer the case.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.9 Step 8: View Audit Records from Realm Violations
You should conduct a periodic review of violations on the unified audit policies that you have created.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access
3.5.10 Step 9: Remove the Components for This Tutorial
You can remove the components that you created for this tutorial if you no longer need them.
Parent topic: Quick Start Tutorial: Securing a Schema from DBA Access